|
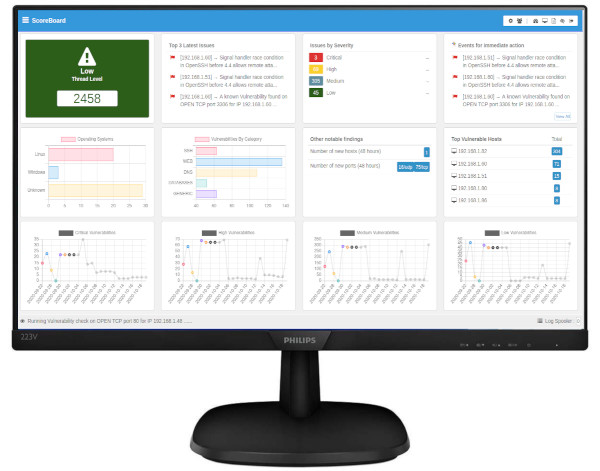
 Penetration TestingPenetration testing, also known as "pen testing," is a simulated cyber attack on a computer system, network, or web application to test its defenses and identify vulnerabilities. It is a valuable service for businesses of all sizes as it helps to protect against real-world cyber threats by proactively identifying and fixing vulnerabilities before they can be exploited by hackers. At CyberX Networks, we offer comprehensive penetration testing services to ensure that your systems are secure. Our team of experienced security professionals uses a variety of techniques and tools to test the defenses of your systems and identify vulnerabilities. We then provide a detailed report of our findings and work with you to develop a plan to remediate any vulnerabilities we discover. Penetration testing is an essential component of a strong cybersecurity program and can help protect your business from data breaches, financial losses, and damage to your reputation. Don't wait until it's too late – contact us today to learn more about our penetration testing services and how we can help secure your systems. Main types of pen testing services offeredThere are two main types of penetration tests: internal and external. Internal penetration tests simulate an attack on a network or system from within the network, as if the attacker had already gained access to the system. This type of test is useful for identifying vulnerabilities that an insider or someone with physical access to the system might exploit. It can also help identify weaknesses in policies, procedures, and employee training. External penetration tests simulate an attack on a network or system from the internet, as if the attacker were a hacker trying to gain unauthorized access from outside the organization. This type of test is useful for identifying vulnerabilities that could be exploited by external attackers, such as those found in web applications or network infrastructure. Both types of penetration tests are important for identifying vulnerabilities and improving the security of a network or system. Internal tests can help identify weaknesses that could be exploited by insiders, while external tests can help identify vulnerabilities that could be exploited by external attackers. By testing both internal and external vulnerabilities, organizations can get a comprehensive view of their security posture and take the necessary steps to protect themselves against cyber threats.
--> |
 Penetration TestingPenetration testing, also known as "pen testing," is a simulated cyber attack on a computer system, network, or web application to test its defenses and identify vulnerabilities. It is a valuable service for businesses of all sizes as it helps to protect against real-world cyber threats by proactively identifying and fixing vulnerabilities before they can be exploited by hackers. At CyberX Networks, we offer comprehensive penetration testing services to ensure that your systems are secure. Our team of experienced security professionals uses a variety of techniques and tools to test the defenses of your systems and identify vulnerabilities. We then provide a detailed report of our findings and work with you to develop a plan to remediate any vulnerabilities we discover. Penetration testing is an essential component of a strong cybersecurity program and can help protect your business from data breaches, financial losses, and damage to your reputation. Don't wait until it's too late – contact us today to learn more about our penetration testing services and how we can help secure your systems. Main types of pen testing services offeredThere are two main types of penetration tests: internal and external. Internal penetration tests simulate an attack on a network or system from within the network, as if the attacker had already gained access to the system. This type of test is useful for identifying vulnerabilities that an insider or someone with physical access to the system might exploit. It can also help identify weaknesses in policies, procedures, and employee training. External penetration tests simulate an attack on a network or system from the internet, as if the attacker were a hacker trying to gain unauthorized access from outside the organization. This type of test is useful for identifying vulnerabilities that could be exploited by external attackers, such as those found in web applications or network infrastructure. Both types of penetration tests are important for identifying vulnerabilities and improving the security of a network or system. Internal tests can help identify weaknesses that could be exploited by insiders, while external tests can help identify vulnerabilities that could be exploited by external attackers. By testing both internal and external vulnerabilities, organizations can get a comprehensive view of their security posture and take the necessary steps to protect themselves against cyber threats.
-->
|


 Login
Login Sign Up
Sign Up