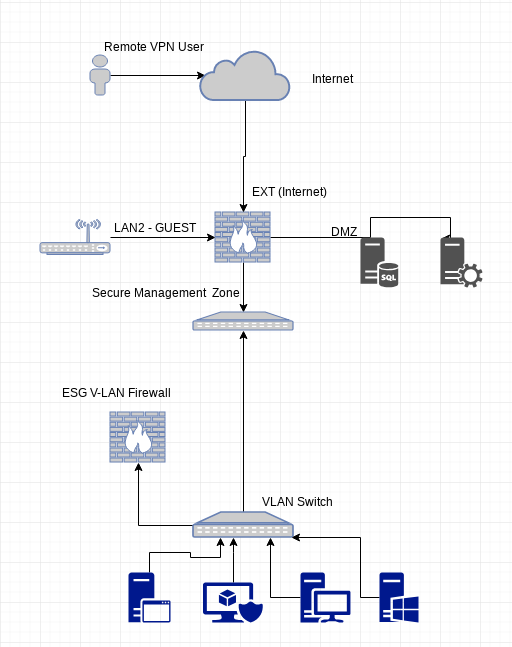
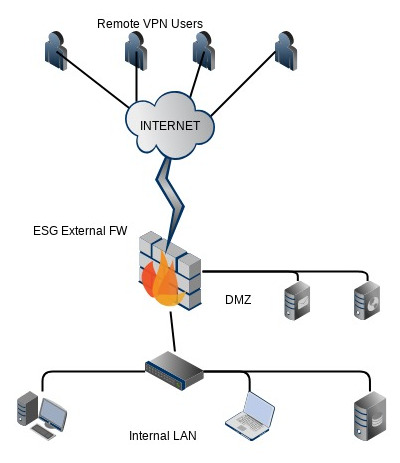
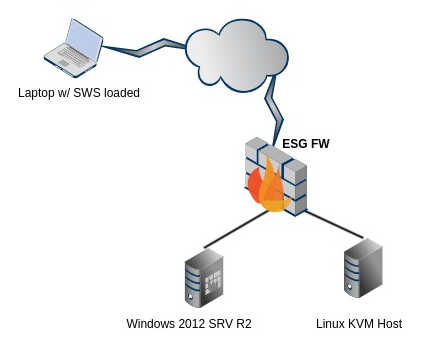
Hi
|
|||||||||||||||||||||||||||||||||||||||||
Hi
|
|||||||||||||||||||||||||||||||||||||||||
CyberX
Web App Firewall
|
[ MODELS & EDITIONS ] [ SCREENSHOTS ] OverviewCyberX's enterprise-class web application firewall (WAF) protects your Internet property from common vulnerabilities like SQL injection attacks, cross-site scripting, and cross-site forgery requests with no or minimal changes to your existing infrastructure. Our core engine fully follows the OWASP standards as for application security. The CyberX team tune,improve and add new signatures and features in order to increase the detection rate and protect you from recent or zero-day attacks.
|
Want to know more ?
|
ProfilingA Web Application Firewall will trigger a lot of false positive if tuned to the maximum. This is due to the variety of web applications around, different languages used and different programming methods. In order to avoid false positives but deliver maximum security, the CyberX engineers create various application profiles for a variate of known web applications and web services. Among others, CyberX WAF has tuned profiles for :
Protection against DDoS attacksThe built-in DDoS protection filters out volumetric attacks before they ever reach your network and harm your apps. It also protects against sophisticated application DDoS attacks without the administrative and resource overhead of traditional solutions, to eliminate service outages. |
Automatic UpdatesAs of all CyberX products, the CxWAF firewall updates automatically through our own controlled repositories. System and application updates run on a daily basic.
Geolocation ControlYour application under your control. Using CyberX WAF geolocation module you can control the access to your application based on geographical location of the incoming request. |
CyberX WAF
Protect your website and Web Applications from cyber threats
|
[ MODELS & EDITIONS ] [ SCREENSHOTS ] OverviewCyberX's enterprise-class web application firewall (WAF) protects your Internet property from common vulnerabilities like SQL injection attacks, cross-site scripting, and cross-site forgery requests with no or minimal changes to your existing infrastructure. Our core engine fully follows the OWASP standards as for application security. The CyberX team tune,improve and add new signatures and features in order to increase the detection rate and protect you from recent or zero-day attacks. |
||||||||||
 |
||||||||||
|
Protection against:
|
||||||||||
ProfilingA Web Application Firewall will trigger a lot of false positive if tuned to the maximum. This is due to the variety of web applications around, different languages used and different programming methods. In order to avoid false positives but deliver maximum security, the CyberX engineers create various application profiles for a variate of known web applications and web services. Among others, CyberX WAF has tuned profiles for :
Protection against DDoS attacksThe built-in DDoS protection filters out volumetric attacks before they ever reach your network and harm your apps. It also protects against sophisticated application DDoS attacks without the administrative and resource overhead of traditional solutions, to eliminate service outages. |
||||||||||
Automatic UpdatesAs of all CyberX products, the CxWAF firewall updates automatically through our own controlled repositories. System and application updates run on a daily basic.
Geolocation ControlYour application under your control. Using CyberX WAF geolocation module you can control the access to your application based on geographical location of the incoming request. |
||||||||||
|
Want to know more ?
|

 Login
Login